COMO FAZER SKIN BONITA NO BONK.IO DE GATO
With the rush for Working From Home, organizations are overwhelmed with employees using video conferencing technologies, from Slack, Skype and Discord to GoToMeeting, Zoom and Webex. What are your security teams supposed to do when incidents like Fairfax school strike? Do they have the basic steps and planned approach to handle the events?. In this page we cover the top tips to analyze and mitigate/contain/remediate […]
ЛИСТИНГ НА GATE.IO
If short on time directly jump to the playbooks section. Summary Any attempt to compromise a system and/or steal information by tricking a user into responding to a malicious message. The most common phishing attacks involve emails armed with malware hidden in attachments or links to infected websites, although phishing can be conducted via other methods such as voicemail, text messages, and social media, too. […]
GATE IO MINIMUM TRADING AMOUNT
Imagine a world where machines can diagnose diseases, write captivating novels, and even hold conversations that feel human. That’s the promise of Artificial Intelligence (AI) and Machine Learning (ML). AI refers to the broad field of computer science dedicated to creating intelligent machines, while Machine Learning is a specific technique where algorithms learn from data to improve their performance on a specific task. These technologies […]
SAFEMOON V2 ON GATEIO
The below use cases are critical to identifying any of the early, middle, and end-stage operations of the threat actors. A small abnormal event can be a clue to a larger adversarial attack. Azure Security Center and Azure Defender are now called Microsoft Defender for Cloud. Azure Security Defaults is enabled on Azure Active Directory Sentinel onehttps://github.com/reprise99/Sentinel-Queries https://github.com/reprise99/Sentinel-Queries/blob/main MCAShttps://www.cloudservus.com/microsoft-cloud-app-security/ Microsoft Defender Office365https://o365blog.com/aadkillchain/ References
GATE.IO TRANSACTION FEES
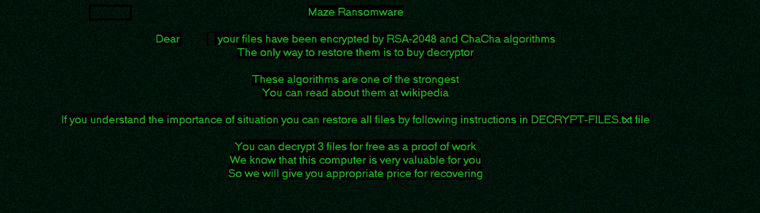
This is required in worst-case scenarios of Ransomware attacks where everything including DR and Backups has failed. This is a critical part of your recovery strategy. Also known as a cyber recovery “clean room”. Understanding normal Disaster Recovery vs. Ransomware Disaster Recovery is key
HTTPS GATE IO ACTIVE 1602085 D67E89D247C1418946CABD416B35FF2B
FlexibleIR helps enterprises prepare for AI cyber incidents and crisis. Here we track the latest AI incidents. What happened and how they happened? We provide you with how you can respond. Below you can find a surated list of websites where we can find AI incidents database. Please free to mail us at contact@flexibleir.com A sample Playbook shown below to handle an incident of training […]
GATE IO LEGIT
Most major cyber attacks have a lot of early warning signals coming in, so early detection helps a lot and gives time for incident response. Logs for Incident Response https://www.first.org/resources/papers/conference2008/chuvakin-anton-slides.pdf Best practises for Event Logging Benefits of continuous and aggressive monitoring of your Event Logging:Enhanced Visibility: Gain a deeper understanding of network activity and potential threats.Faster Incident Response: Early Detection and quick response to security […]
GATE.IO WHERE IS IT LOCATED
Enterprises are going to adopt a wide range of Generative AI use cases. The security teams need to understand them, and how they are built so they can eventually protect it better. Here we are learning from the perspective of Incident Response to cyber attacks on the AI platforms. Case study 1 – A great CTI tool – Neutocti This project gives a great insight […]